Address
1st Floor New Rehema House, Rhapta Road, Westlands, Nairobi, Kenya
Work Hours
Monday to Friday: 8:30AM - 5PM
Address
1st Floor New Rehema House, Rhapta Road, Westlands, Nairobi, Kenya
Work Hours
Monday to Friday: 8:30AM - 5PM


Never miss our insights — stay up to date with the latest trends in audit, tax, and advisory services.
Never miss our insights — stay up to date with the latest trends in audit, tax, advisory, and business consulting
Introduction
Cloud computing refers to the on-demand delivery of computing services, including infrastructure, platforms, and software through models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). These models offer businesses scalability, flexibility, and cost-efficiency. As the cost of maintaining on-premises infrastructure continues to rise, many organizations have increasingly adopted cloud solutions to improve operations and reduce capital expenditures.
However, realizing the full benefits of cloud computing depends heavily on proper configuration and management. The pay-as-you-go nature of cloud services allow organizations to provision resources when needed and release them when no longer in use. Despite these advantages, mismanagement such as failing to decommission unused resources can lead to significant operational costs. Additionally, the complexity of cloud environments introduces critical security challenges that must be proactively addressed.
Common Cloud Security Risks
Incorrectly configured cloud environments are a leading cause of vulnerabilities. Errors during resource provisioning or access control setup can expose systems to unauthorized access and data breaches.
Application Programming Interfaces (APIs) facilitate interaction between cloud services and applications. When poorly designed or unsecured, APIs can serve as entry points for attackers, increasing the system’s attack surface.
Access management defines how user permissions are structured and enforced. Improper configurations can lead to privilege escalation or unauthorized access.
Cloud platforms often operate on a shared infrastructure model. As a result, vulnerabilities in the underlying infrastructure can affect multiple tenants, exposing cloud consumers to inherited risks.
These attacks exploit previously unknown vulnerabilities for which no patches exist. Cloud environments lacking timely detection and response mechanisms are particularly vulnerable to zero-day threats.
Sophisticated attackers may employ techniques such as rootkits, lateral movement, DNS tunnelling, or social engineering to establish long-term access to cloud environments. Once inside, they can exfiltrate data, manipulate resources, or deploy ransomware.
Cloud providers often mandate baseline security practices. However, many organizations fail to implement or maintain compliance with these standards, leaving their environments exposed to regulatory and cybersecurity risks.
Case Study
One of the cloud players, Citrix recently unearthed a possible vulnerability, CVE-2025-5777: Citrix Bleed 2, in their system where attackers could possibly gain initial access to cloud environments. Though not fully exploited, their alert notice made public knowledge of its potential use for unauthorized access to cloud environments.
An original Version of the exploit which targeted Citrix NetScaler called Citrix Bleed allowed attackers to extract session cookies directly from memory, enabling them to bypass MFA and hijack user sessions. A similar technique was used on Boeing, making it such a serious attack.
Citrix faced a major backlash after the Citrix Bleed of 2023 due to poor communication with their customers, and the level of guidance to security teams in addressing vulnerability.
Protecting Cloud Environments
Adopting effective cloud security strategies can be daunting, however bodies such as the Cloud Security Alliance (CSA) provide implementation guides for securing any cloud environment. As a business whether beginning or maturing in cloud adoption, you can take the following steps to secure your cloud environment.
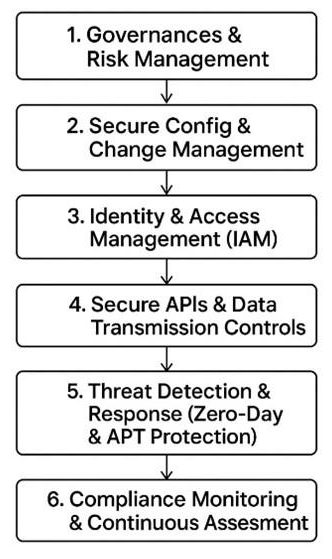
Establish baseline policies, roles, and responsibilities for cloud security through conducting cloud risk assessments & having risk registers, define policies for data handling and vendor access, classify data assets and map them to appropriate controls.
Ensure cloud resources are provisioned securely and maintained through a structured change control process by use of Infrastructure as Code (IaC), using hardened images, continuous monitoring tools and proper change management to review before deployments.
Enforce the least privilege access to cloud assets and services through RBAC, SSO, MFA, access log review, Just In Time (JIT) access and API key rotation.
Protect data in transit and prevent exploitation via insecure APIs through TLS encryption, validating all API inputs, and using API gateways to monitor traffic.
Continuously monitor threats and proactively respond to them by using tools such as SIEM, SOAR, XDR and EDR solutions that are fine-tuned to minimize false positives.
Continuously validate alignment with compliance and security benchmarks using automated audits, mapping controls, generating audit reports and taking corrective actions, and maintaining evidence of compliance posture.
Conclusion
Given the complexity of securing cloud environments and maintaining compliance, we at Baker Tilly are here to support you. Visit our website at https://bakertilly.ke or reach out to our team at john.mucheru@bakertilly.ke and javan.ayoma@bakertilly.ke to help you assess your cloud infrastructure, strengthen your security posture, ensure regulatory compliance, and help you maximize return on investment while minimizing exposure to external breaches while in the cloud.